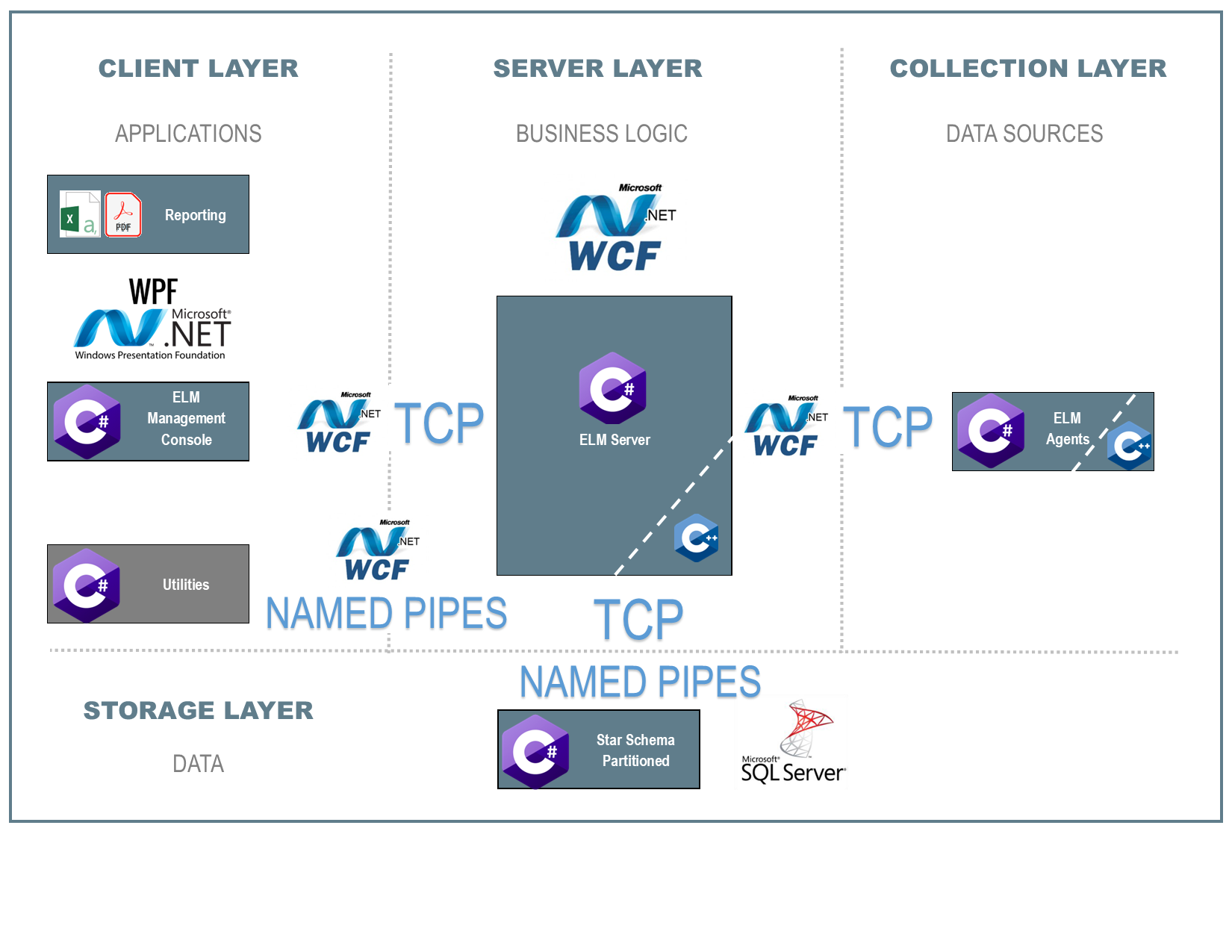
Our Technologies
ELM Enterprise Manager is developed on a Microsoft foundation with mainstream languages, applications, and tools. Our development goal has been to strictly adhere to best practices, utilize mainstream technologies, and support the latest and largest segment of Windows operating systems available.
We don’t like being held hostage by proprietary technologies and we don’t think our customers do either. ELM stores collected data in Microsoft SQL databases that have been optimized for the best efficiency and use of space. This means that you can access your data with the tools you prefer. And you can take your data with you should you choose to move on to another monitoring product. It’s your data.
Programming Languages and Communication Protocols:
- Microsoft C++
- Microsoft C# / .Net Framework
- Windows Presentation Foundation (WPF)
- Windows Communication Foundation (WCF)
- TCP
- Named Pipes
Protecting Data – Security & Encryption
ELM uses integrated Windows Security (NTLM or Kerberos depending on the Server and Agent OS) for authenticating users. Each of the components that make up ELM can be secured at a granular level, enabling administrators to delegate permissions to individual users, groups or class of user.
ELM Server
At the server level, AES-256 bit encryption with Transport Level Security (TLS) over TCP is utilized for communication between the server and the Management Console.
Agent to Server & Server to Server
Data passed from agents to the server, or from one server forwarding events to another server in a N-tier architecture, utilize AES-256 bit encryption with authentication by IP address. Events forwarded from a legacy ELM server utilize AES-128 bit encryption.
SQL Databases
The client-server communications to the database are performed utilizing a Microsoft .NET client over TCP or Named Pipes depending on the SQL Server configuration. All security is defined by the SQL Server.