ELM uses integrated Windows Security (NTLM or Kerberos depending on the Server and Agent OS) to authenticate users. Some of the functions won't work (such as killing a task or managing services) unless you have administrative rights on the monitored computer. ELM supports object and item-level security through the snap-in UI. You may apply Windows Access Control Lists (ACLs) to objects in your ELM Console.
DCOM Permissions
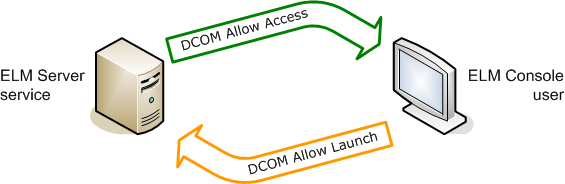
Communication between the ELM Server and the ELM Console or ELM Advisor is done with Distributed COM (DCOM). The ELM Server service requires DCOM Allow Access permissions to the ELM Console and ELM Advisor. In turn, users running the ELM Console or ELM Advisor require DCOM Allow Launch permissions to the ELM Server.
DCOM Allow Access permissions are granted to the Authenticated Users group by the ELM setup program when the ELM Console is installed. This automatic configuration is denoted by the green arrow in the diagram below. DCOM Allow Launch permissions need to be granted on the ELM Server computer by an Administrator. This manual configuration requirement is denoted by the orange arrow in the diagram below.
These permissions may be viewed and edited via the DCOM Configuration Utility (DCOMCNFG.exe). To manage these permissions, use the steps below.
Allow Access
These steps should be done automatically by ELM setup.
In Windows XP, Vista, Windows 7, Windows 2003, or Windows 2008:
1.Launch DCOMCNFG.
2.Expand Component Services, then Computers, then My Computer, and finally DCOM Config.
3.Scroll down to ELM.Advisor.exe.
4.Right-click and select Properties.
5.Select the Security tab.
6.In the Access Permission area, click the Edit button.
7.Verify that Authenticated Users has Allow for Local Access and Remote Access.
8.Repeat steps 3-7 for MMC Application Class.
Note
In some cases, the ELM Setup package does not have permissions to the MMC Application Class DCOM application. When this happens you will typically see the Use Default radio button selected, and Authenticated Users will be granted Access at the My Computer level.
9.Close DCOMCNFG.
You may have to reboot each system in order for the DCOM security changes to take effect.
Allow Launch
These steps need to be manually verified and completed, as necessary.
In Windows XP, Vista, Windows 7, Windows 2003, or Windows 2008:
1.Launch DCOMCNFG.
2.Expand Component Services, then Computers, then My Computer, and finally DCOM Config.
3.Scroll down to TNT Software .
4.Right-click and select Properties.
5.Select the Security tab.
6.In the Launch and Activation Permissions area, select the Custom radio button, and click the Edit button.
7.Verify that ELM Console users, or an equivalent group, have Allow for Local and Remote, Launch and Activation.
8.Close DCOMCNFG.
You may have to reboot each system in order for the DCOM security changes to take effect.
Note
Because communication between an ELM Server and an ELM Console is COM-based, TCP port 135 (RPC endpoint mapper) must be open between the communicating end-points. DCOM also uses RPC dynamic port allocation. By default, RPC dynamic port allocation randomly selects port numbers above 1024. You can control which ports RPC dynamically allocates for incoming communication and then configure your firewall to confine incoming external communication to only those ports (and TCP/UDP port 135).
NetBIOS/RPC
When using a Virtual Agent to monitor a Windows system (e.g., to collect events, monitor services, etc.), monitoring is performed by the ELM Server. The ELM Server makes RPC Win32 API calls to execute Monitor Items and collect data. There must be NetBIOS and RPC connectivity between the ELM Server and the Virtual Agent.
Firewalls and Port Blocking
If you intend to use Virtual Agents in a firewall environment (IE putting a firewall between the ELM Server and ELM Virtual Agent), or put a firewall between the ELM Server and ELM Console, network communication is RPC based. TCP port 135 (RPC endpoint mapper) must be open between the communicating end-points. DCOM also uses RPC dynamic port allocation. By default, RPC dynamic port allocation randomly selects port numbers above 1024. You can control which ports RPC dynamically allocates for incoming communication and then configure your firewall to confine incoming external communication to only those ports (and TCP/UDP port 135).
For more information on DCOM and firewalls, see Microsoft's White Paper about Using DCOM with Firewalls.